Have you ever wanted to train your organisation to fight Russian influence operations? Now you can! This article explains how to use Conducttr to implement a Russian influence operation based on the techniques described in various research papers like this one, and this one. Plus research and advice from organisations like Graphika and First Draft.
Here are the steps we’ll follow:
- 1. Know what you want to achieve – understanding the Information Environment
- 2. Create your influence network
- 3. Understand the Russian influence operations playbook
- 4. Design your event and plot how the conversation spreads
- 5. Implement the injects
1. Understanding the Information Environment
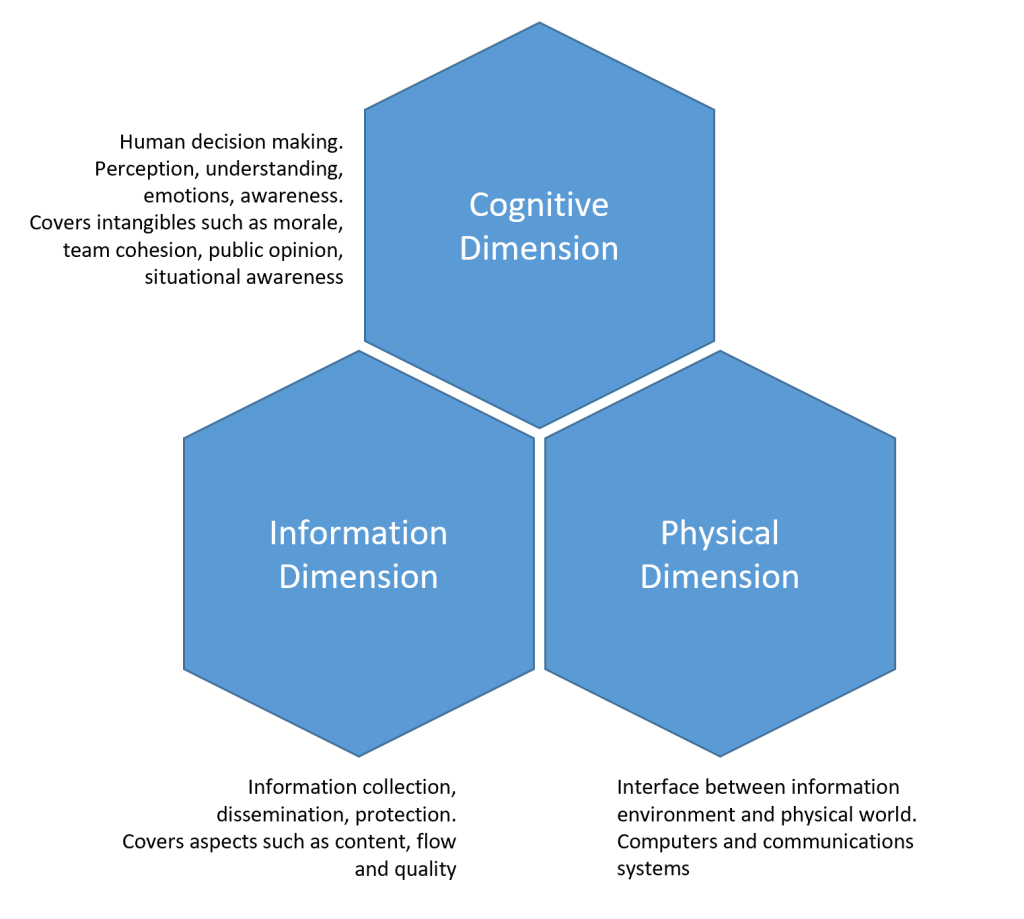
The diagram below is a common explanation for what is meant by the information environment.
The Cognitive Dimension can be thought of as our effects or end goal. What is it that we want to achieve with this influence operation that affects the mind of our adversary? The effect could be anything from perception to morale. If you’re looking for behavioural changes then that’s a higher order so you might want to start with the behavioural outcome and then come down to how you’d achieve that with a cognitive effect.
The Information Dimension is where we’ll build our exercise in Conducttr – this is where we decide what content needs to be where and at what time. It’s here we have to consider how our message will spread – as we do in this previous blog post.
The Physical Dimension is the tangible part that allows our messaging to be delivered – the communications network, computers, phones etc. This dimension is the realm of electronic warfare which we won’t concern ourselves with here. For anyone interested in broader Information Operations, this document is an interesting place to start.
2. Create the Influence Network
Our influence network needs to replicate a mix of Russian government spokespeople & institutions, State-sponsored media like RT, and proxies – witting and unwitting media outlets, journalists and influencers. This is described very well in this document: Pillars of Russia’s Disinformation and Propaganda Ecosystem. Similar work can be found here “How Russia manages its political war in Europe”
In Conducttr jargon, these are our personas from which we’ll deliver our content. For simulating fake journalists that are IRA sock puppets, there is of course https://thispersondoesnotexist.com/ and for others, remember to create a recent create date within the last month or so and for any bots use a handle with a 4- to 8-digit number like RP565212 or similar.
Depending on the type of exercise, you might now want to build a social graph between the personas – this will give the training audience half a chance of tracing the associations ahead of any inauthentic behavior.
To simulate coordinated inauthentic behaviour, we have a few options. The easiest is to use our pattern of life feature and create a stack of content that uses custom data. Think of custom data as a set of variables that will allow you to reuse the same content multiple times. This could be to simulate coordinated retweets or calls to “get this hashtag trending” or used with dynamic images as if copy-pasting the same content across accounts (as the Graphika article here).
For less-easy-to-spot coordination you’ll have to use the Master Events List and chain content in a way that simulates the laundering of disinformation and the amplification by bigger players. And that’s explained in the remaining steps…
3. The Russian playbook
Use real-world examples from research like this from Graphika and this from NATO StratComCoE (Information Laundering in Germany). The site EUvsDisinfo is also an excellent source of examples.
4. Design the information spread
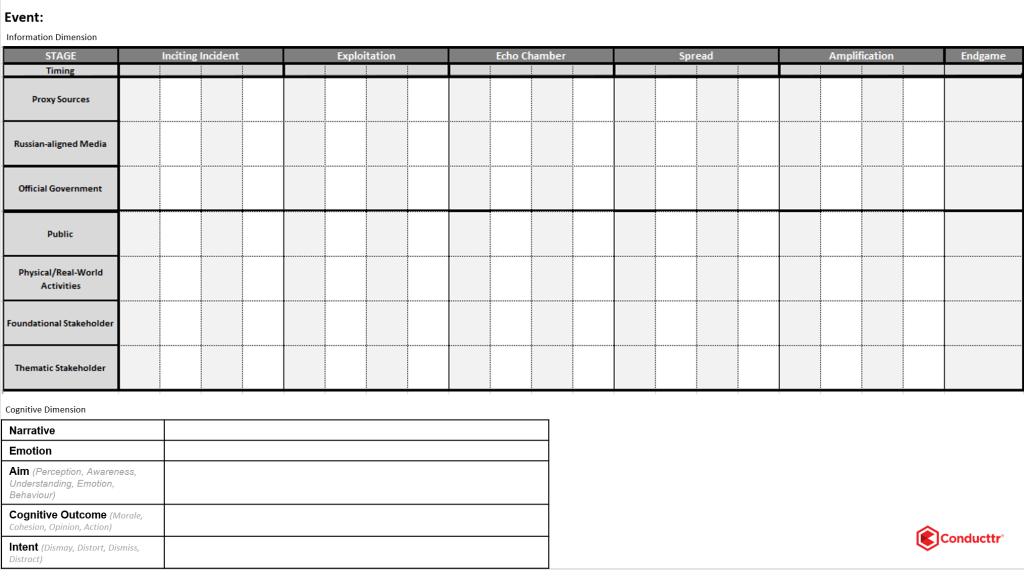
The image below shows our Russian influence operations planning sheet to plot the simulated trajectory of your message. The concept is that some inciting event happens online or in the real world and then the information spreads in a typical way from left to right. The stages aren’t the same duration and some might be skipped completely if the news breaks directly with someone with a large audience. Hence, give consideration to your growth curve: slow burn or rapid rise?
Slow burn will likely mean you want to launder your disinformation through several blogs or smaller, factional “news” organisations so that the original lie from a poorly trusted source becomes slowly hidden after being repeated by trusted sources as fact. This happens by passing the message through different personas at different stages.
Rapid rise will mean you’ll need to get national, regional or international exposure quickly via a State official, major media outlet or an influencer with a large following during the Exploitation phase.
Try to start by completing the Cognitive Dimension fields because this is your objective. Note that we’re using the 4D model but Distort and Dismay are more likely to be objectives because Dismiss and Distract tend to be reactions rather than intentions.
The stages are:
Inciting incident – The initial act that triggers the chain
Exploitation – The act that makes the most of the inciting incident
Echo Chamber – The faction eager to seize on the inciting incident but hears it first from the exploitation actor
Spread – The first breakout moment when the news leaves the eager and engages the middle ground
Amplification – The news hits an influencer or media org with significant reach
End game – When this event ends (for now)
5. Implement the injects
That’s it, you reached the end and now all that’s left is to write your Russian influence operation content!
To ensure authenticity, your personas will want to use the same hashtags and lexicon, and when you get to the spread and amplification stages you’ll possibly want calls to action rather than just complaints and opinion. Our post on creating a Twitterstorm will help a little here.
Good luck, Comrade!
ps. If you’re interested to know how to counter influence operations, there’s some good advice in this Belfer Center document, the IO Playbook Part 2. Part 1 is here: IO Playbook